End-to-End Identity Management Framework ...
Framework:
As the global marketplace continues to expand, new and innovating ways of
conducting business are becoming a necessity in order to maintain corporate
security practices and remain in compliance with existing governmental
regulations. In order to keep sensitive data within the hands of the right
people, more and more corporations are seeking out multi-layer identity
management solutions. Although the core of any robust Identity Management (IdM)
architecture lies within its user provisioning capabilities, there are multiple
components necessary to keep application data secure.
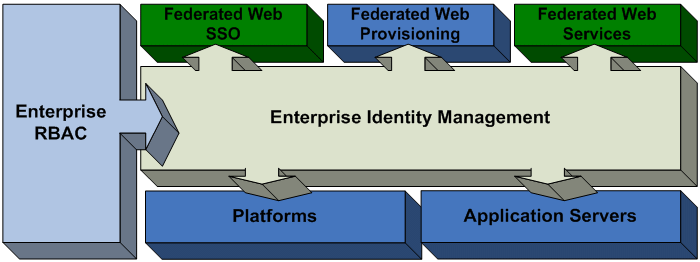

End-to-End Strategy:
NetworkingPS' product and services
offerings in the Security Management space all correspond to this multi-layer
model of identity management, from fundamental user provisioning and
administrative capabilities to fine-grained application role management.
NetworkingPS’ end-to-end identity management strategy consists of the following
elements:
- User Provisioning
-
Automated Account Management
-
User Lifecycle Management
-
Real-time Administration of User Privileges and
Attributes
-
User Event Logging
-
Password Management
-
Reporting
-
Role Management
-
Discovery, Definition and Cleanup of Existing Roles
through Automated Role Mining
-
Real-time Enforcement of User Roles
-
Enterprise-wide management of formal and informal
business-level roles
-
Linkage between business roles and IT roles
-
Lifecycle Management of Roles: role owner, role
changes, role review, role assignment and role retirement
-
Creating a consistent development process for new
roles and tying those roles into an automated role management solution
-
Access Management
-
Federated User Provisioning
-
Single Sign On for Web-based Applications and Web
Services-Enabled Applications
-
Single Sign On for Federated Applications
-
Defined user access controls based on minimum
requires necessary to perform job functions


For More
Information
To download information about this and other NetworkingPS Security Management
Services offers, please click
here.
|
